2.3
Strengths and Limitations of Each Technique
Each watermarking technique has its own strengths and limitations. Spatial domain techniques are simple and computationally efficient but may be less robust against certain attacks [5]. Frequency domain techniques offer better robustness but may be more computationally intensive and sensitive to synchronization issues [5]. Hybrid techniques aim to balance the trade-off between robustness and imperceptibility but may be more complex to implement [3]. Reversible watermarking ensures the integrity of the original content but may have limited capacity for watermark embedding [4].
+
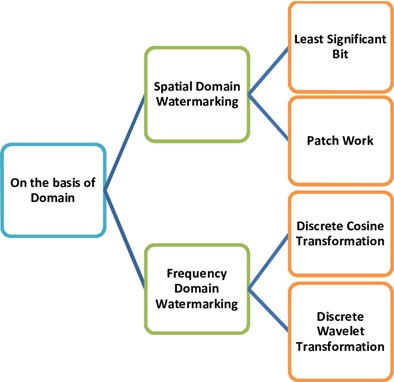
Fig. 10: Pipeline of spatial domain and frequency domain watermarking
The choice of watermarking technique depends on the specific application requirements, such as the desired level of robustness, imperceptibility, and computational efficiency [6]. Watermarking methods are generally more robust and resistant to various signal processing attacks compared to spatial domain techniques.
+
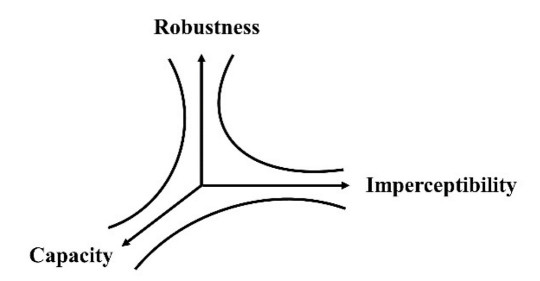
Fig. 11: Chart depicting the trade-off between robustness, imperceptibility, and capacity in watermarking techniques
Advantage
Strengths:
- Serves as a clear deterrent against unauthorized use, providing immediate visual proof of ownership and copyright.
- Enables easy identification of the content creator or owner, discouraging potential infringers.
- Allows for the inclusion of branding elements, such as logos or company names, enhancing brand visibility and recognition.
- Can be customized in terms of size, opacity, and placement to strike a balance between protection and visual appeal.
Disadvantage
Limitations:
- May affect the aesthetic appeal of the content, particularly when the watermark is large or prominently placed.
- Can be distracting to viewers, potentially impacting their enjoyment or perception of the content.
- Vulnerable to simple attacks, such as cropping or removal using image editing tools, especially if the watermark is placed in a static position.
- May not provide sufficient protection against determined attackers with advanced editing skills and tools.
Practice
Real-life scenarios:
Resistant: A stock photography website applies visible watermarks to all preview images, ensuring that potential buyers cannot use the images without purchasing the rights. An attacker attempts to remove the watermark using basic editing tools but finds that the watermark is carefully integrated into the image, making it difficult to remove without significantly degrading the quality.
Vulnerable: A digital artist shares a watermarked version of their artwork on social media to protect their intellectual property. However, an attacker with advanced image editing skills carefully removes the watermark, creating a near-identical copy of the artwork without the artist's branding, and proceeds to sell the artwork as their own.
Advantage
Strengths:
- Protects content without affecting its visual quality, allowing for the discreet embedding of copyright information and other metadata.
- Can be used to track the distribution and usage of content, enabling content owners to monitor and enforce their rights.
- Provides a higher level of security compared to visible watermarks, as the presence of the watermark is not easily detectable by casual observers.
- Allows for the embedding of more robust and complex watermarks that can withstand various signal processing attacks.
Disadvantage
Limitations:
- Requires specialized tools and knowledge to detect and extract the embedded watermarks, making it less accessible for the average user.
- May be vulnerable to sophisticated signal processing attacks and geometric distortions, which can degrade or remove the watermark without significantly impacting the content quality.
- The imperceptibility of the watermark may make it less effective as a deterrent against casual infringement, as the presence of the watermark is not immediately apparent.
- The embedding process may introduce subtle artifacts or distortions in the content, particularly if a high-capacity or robust watermark is used.
Practice
Real-life scenarios:
Resistant: A video streaming platform employs invisible watermarking to embed unique user identifiers in each video stream. When an attacker captures and redistributes a stream without authorization, the platform can extract the watermark, identify the source of the leak, and take appropriate action, such as terminating the user's account or pursuing legal recourse.
Vulnerable: A medical imaging device uses invisible watermarking to authenticate and protect sensitive patient data. An attacker with knowledge of the specific watermarking algorithm exploits a weakness in the system, allowing them to modify the watermarked images and tamper with the patient data without triggering any alarms or warnings.
Advantage
Strengths:
- Computationally efficient and relatively simple to implement, making it suitable for real-time applications or resource-constrained devices.
- Resistant to global transformations, such as brightness or contrast adjustments, the watermark is embedded directly into the pixel values.
- Allows for the embedding of high-capacity watermarks, enabling the inclusion of more information or multiple watermarks within the content.
- Can be easily integrated into existing image processing workflows and systems.
Disadvantage
Limitations:
- Less robust against geometric distortions, such as rotation, scaling, or cropping, which can disrupt the spatial synchronization of the watermark.
- Vulnerable to pixel-level modifications, such as compression, noise addition, or local tampering, which can degrade or remove the watermark.
- May introduce visible artifacts or distortions in the content, especially if a high-capacity or strongly embedded watermark is used.
- The watermark may be more easily detectable or extractable by attackers compared to frequency domain techniques.
Practice
Real-life scenarios:
Resistant: A digital document management system employs spatial domain watermarking to embed copyright information and user permissions directly into the document images. An attacker attempts to modify the permissions by applying global transformations, such as adjusting the brightness or contrast, but the watermark remains intact and detectable, preventing unauthorized access.
Vulnerable: A social media platform uses spatial domain watermarking to embed user profile information into shared images. An attacker applies a combination of noise addition and local tampering techniques to specific regions of the image, effectively removing the watermark without significantly degrading the overall image quality.
Advantage
Strengths:
- Provides better robustness against common signal processing attacks, such as compression, filtering, and noise addition, as the watermark is spread across the frequency spectrum.
- Allows for the embedding of more imperceptible watermarks, as the modifications are made in the frequency domain rather than directly to the pixel values.
- Enables better synchronization and resilience against geometric distortions, as the watermark can be designed to be invariant to certain transformations.
- Offers more flexibility in terms of watermark design and adaptation to specific content characteristics or application requirements.
Disadvantage
Limitations:
- Computationally more intensive compared to spatial domain techniques, requiring additional time and resources for the embedding and extraction processes.
- May introduce visible artifacts or distortions in the content, particularly if the watermark is embedded in perceptually significant frequency bands.
- The effectiveness of the watermark may be limited by the characteristics of the host content, such as the presence of strong edges or textures that can mask the watermark.
- Requires careful design and selection of the frequency bands and embedding strengths to achieve a balance between robustness and imperceptibility.
Practice
Real-life scenarios:
Resistant: A digital rights management (DRM) system employs frequency domain watermarking to embed license information and usage restrictions into multimedia content. An attacker attempts to remove the watermark by applying various signal processing operations, but the watermark remains detectable in the frequency domain, enabling the DRM system to enforce the usage rules.
Vulnerable: An online marketplace uses frequency domain watermarking to embed seller information into product images. An attacker exploits a vulnerability in the watermarking algorithm, allowing them to estimate and remove the watermark components from specific frequency bands without causing noticeable distortions in the image, effectively erasing the seller information.
Advantage
Strengths:
- Combines the advantages of both spatial and frequency domain techniques, achieving a balance between robustness and imperceptibility.
- Provides multiple layers of protection, as the watermark is embedded in both domains, making it more difficult for attackers to completely remove the watermark.
- Allows for the adaptation of the watermarking scheme to the specific characteristics of the content and the anticipated types of attacks.
- Enables the incorporation of error correction and detection mechanisms to enhance the reliability and integrity of the watermark.
Disadvantage
Limitations:
- Increases the complexity of the watermarking system, requiring more sophisticated embedding and extraction algorithms and higher computational resources.
- May introduce additional processing overhead and delays, particularly for real-time applications or large-scale deployments.
- The effectiveness of the hybrid approach may be limited by the inherent weaknesses of the individual spatial and frequency domain techniques used.
- Requires careful design and parameter tuning to ensure optimal performance and to avoid potential conflicts or interference between the watermarks in different domains.
Practice
Real-life scenarios:
Resistant: A cloud-based media storage and sharing platform employs hybrid watermarking to protect user-uploaded content. The watermark is embedded in both the spatial and frequency domains, with each domain targeting different types of attacks. When an attacker attempts to remove the watermark using a combination of spatial and frequency-based techniques, the multi-layered protection ensures that the watermark remains detectable, enabling the platform to identify and block the unauthorized distribution of the content.
Vulnerable: A government agency uses a hybrid watermarking system to authenticate and protect sensitive satellite imagery. An attacker with insider knowledge of the specific hybrid watermarking algorithm employed by the agency exploits a weakness in the system, allowing them to carefully remove the watermark components from both the spatial and frequency domains without raising suspicion. The attacker then proceeds to leak the modified imagery, compromising national security.
Advantage
Strengths:
- Allows for the complete restoration of the original host content after watermark extraction, ensuring the integrity and authenticity of the content.
- Enables the embedding of sensitive or critical information, such as medical data or legal documentation, without permanently altering the original content.
- Provides a higher level of trust and assurance to users, as they can verify that the watermarked content can be fully restored to its original state.
- Facilitates the development of secure and privacy-preserving applications, where the watermark can be used for authentication or data hiding without compromising the content itself.
Disadvantage
Limitations:
- Imposes additional constraints on the watermarking scheme, as the embedding process must be designed to allow for perfect reversibility.
- Typically has a lower embedding capacity compared to non-reversible techniques, limiting the amount of information that can be embedded.
- May be more computationally complex and resource-intensive, as the reversibility requirement adds an extra layer of processing and data management.
- The reversibility property itself may be exploited by attackers to remove the watermark or to hide their own malicious data within the watermarked content.
Practice
Real-life scenarios:
Resistant: A healthcare provider uses reversible watermarking to embed patient information and diagnostic data into medical images. The watermark ensures the authenticity and integrity of the images while allowing for the complete restoration of the original content when needed for critical medical procedures or legal purposes. An attacker attempts to tamper with the watermarked images but finds that any modifications are easily detectable, and the original images can be perfectly recovered, maintaining the trust and reliability of the medical records.
Vulnerable: A digital archive employs reversible watermarking to embed metadata and provenance information into historical documents and artifacts. An attacker discovers a flaw in the reversible watermarking algorithm that allows them to extract the watermark data without triggering any alarms. The attacker then exploits this vulnerability to surreptitiously modify the metadata, altering the historical context and provenance of the artifacts without leaving any detectable traces.